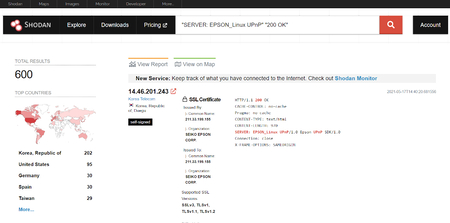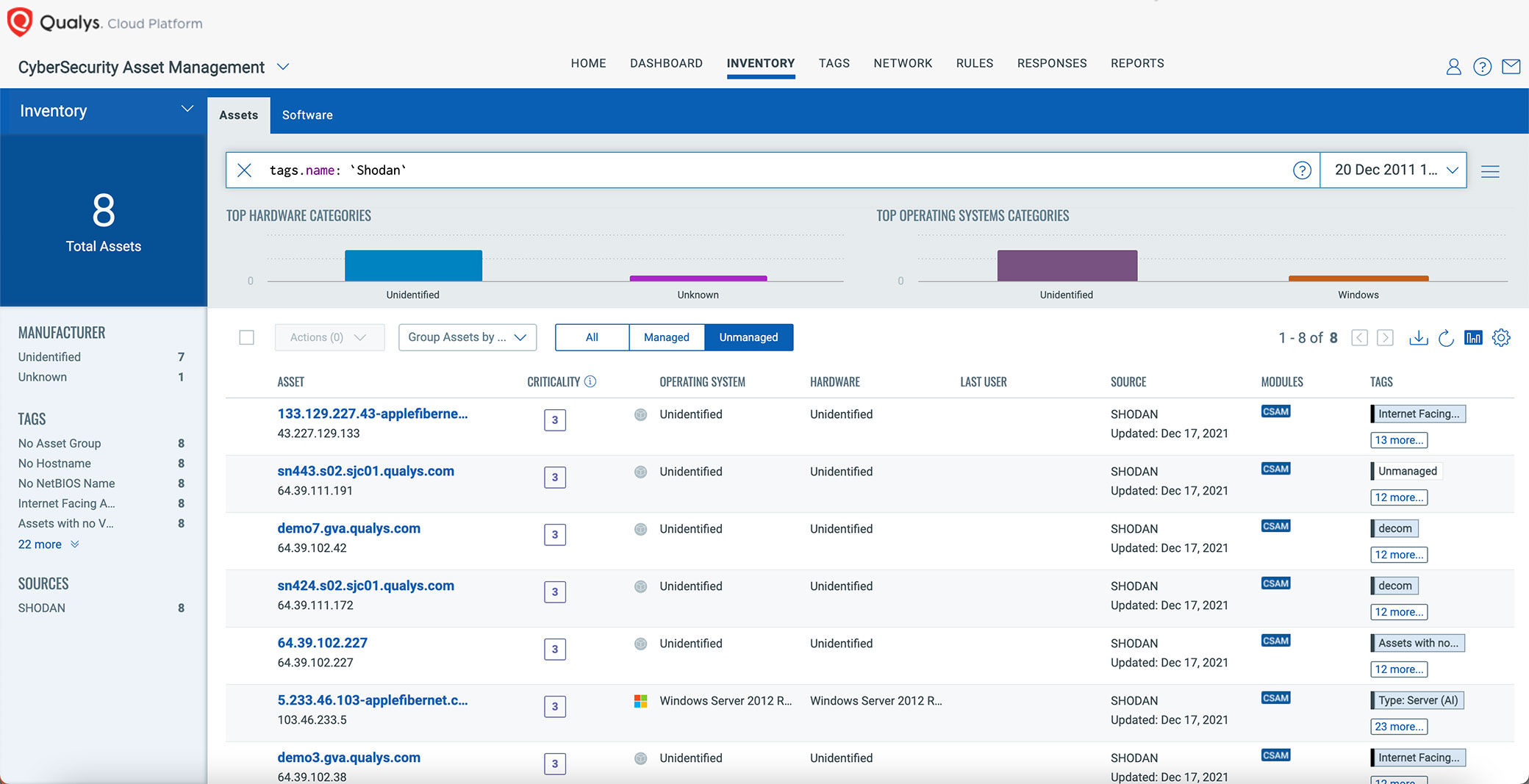
Sensors | Free Full-Text | Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases

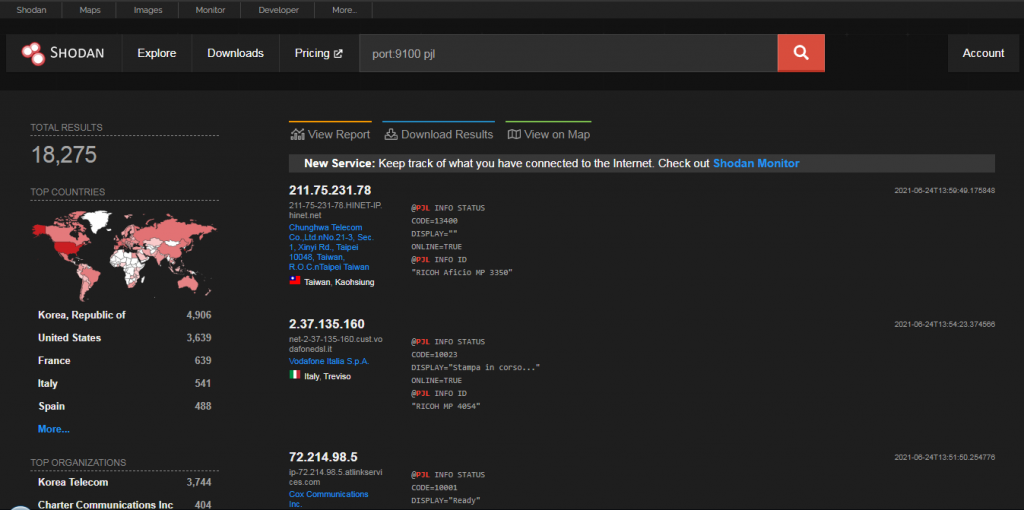
Insights from the PewDiePie Hack: Trends in Strengthening Public Sector Printer Security – Connected IT Blog



![Complete Guide to… by John Matherly [Leanpub PDF/iPad/Kindle] Complete Guide to… by John Matherly [Leanpub PDF/iPad/Kindle]](https://d2sofvawe08yqg.cloudfront.net/shodan/s_hero2x?1620485817)